In the ever-evolving landscape of technology, where innovations disrupt and transform industries at a rapid pace, a new paradigm in software architecture is emerging WADWARE. This groundbreaking concept, born from the fusion of “WAD” (Wide Area Distributed) and “WARE” (Software), promises to revolutionize the way we conceive, develop, and deploy software solutions. In this comprehensive exploration, we delve into the depths of uncovering its transformative potential, applications across industries, challenges, and opportunities it presents, and strategies to embrace this future-forward approach to software development.
Table of Contents
ToggleUnveiling WADWARE: A Paradigm Shift in Software Architecture
WADWARE represents a seismic shift from traditional software models, transcending the limitations of localized systems by harnessing the power of distributed computing over expansive geographical regions. At its core embodies scalability beyond limits, enhanced reliability, and redundancy, thus laying the groundwork for unprecedented innovation and efficiency. Let’s delve deeper into the foundational elements that propel it into the forefront of the digital era.
The Power of Wide Area Distributed Computing
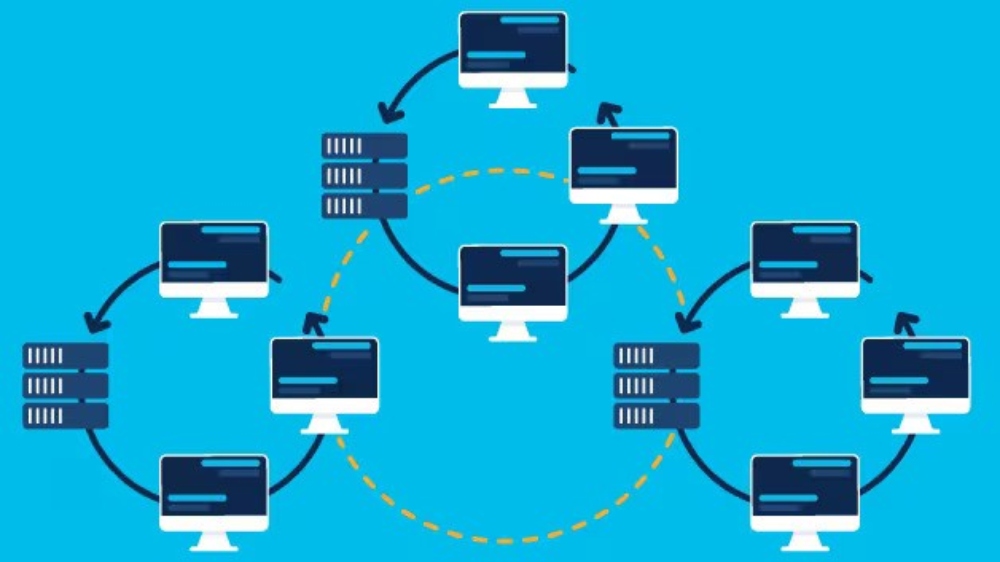
Central to the essence of WADWARE lies the harnessing of wide area distributed computing, where software applications transcend boundaries, seamlessly operating across diverse geographical locations. By decentralizing data and processing tasks across multiple nodes not only enhances performance but also fortifies system robustness, mitigating the risk of single points of failure and downtime.
Scalability Beyond Limits
One of the hallmarks is its unparalleled scalability, a feat unattainable within the confines of traditional software architectures. While conventional systems struggle to accommodate growing user bases or expanding functionalities thrives on scalability, effortlessly adapting to the evolving demands of the digital landscape.
Enhanced Reliability and Redundancy
Integrating WADWARE into software solutions introduces a new paradigm of reliability and redundancy, unparalleled by its predecessors. With data and processing distributed across a multitude of nodes, the vulnerability to system failures diminishes significantly, ensuring a resilient and dependable infrastructure.
Applications Across Industries: Transforming the Landscape
The transformative potential reverberates across a myriad of industries, reshaping paradigms and unlocking new avenues for innovation. From optimizing complex logistics operations to revolutionizing healthcare data systems, the versatility positions it as a disruptive force driving efficiency, cost reduction, and enhanced user experiences.
Security Measures in WADWARE: Safeguarding the Digital Frontier

Amidst the transformative potential of concerns regarding security naturally arise. However is engineered with robust security protocols, incorporating encryption and authentication measures to fortify data integrity and user privacy. Furthermore, the distributed nature of the architecture inherently bolsters resilience against potential cyber threats, ensuring a fortified digital frontier.
Navigating the Road Ahead: Challenges and Opportunities
While the promise of WADWARE is boundless, navigating the path towards its widespread adoption entails a spectrum of challenges and opportunities. Organizations seeking to integrate into their systems must navigate technical transitions, evolve skillsets, conduct thorough cost-benefit analyses, and ensure compliance with regulatory frameworks. However, amidst these challenges lie unprecedented opportunities for innovation, collaboration, and technological advancement.
Technical Transition and Integration: Evolutionary Imperatives
Transitioning from conventional software architectures to necessitates meticulous planning and execution. Developers must adapt their coding practices to leverage the distributed nature of effectively, while existing systems may require substantial modifications to accommodate this paradigm shift. Moreover, ensuring compatibility and interoperability poses significant challenges that demand strategic foresight and technical acumen.
Skillset Evolution: Nurturing Talent for the Future
As WADWARE redefines the landscape of software development, the demand for professionals skilled in distributed computing and wide-area networking escalates. Organizations must prioritize upskilling their teams or recruiting experts proficient in the intricacies of this transformative technology, laying the foundation for sustained innovation and growth.
Opportunities for Innovation and Collaboration: Pioneering New Frontiers
Amidst the challenges of adoption heralds a new era of innovation and collaboration, transcending boundaries and fostering synergistic endeavors across industries. Developers and organizations are poised to pioneer groundbreaking solutions, leveraging the distributed capabilities to create resilient, efficient, and user-centric applications that redefine industry standards.
Cost-Benefit Analysis: Balancing Investment and Returns
While the allure of scalability and efficiency underpins the value proposition of organizations must conduct comprehensive cost-benefit analyses to ascertain the viability of adoption. While initial investments in infrastructure, training, and development may be substantial, the long-term dividends in terms of performance, reliability, and innovation can outweigh these costs, positioning as a strategic imperative for future-proofing digital ecosystems.
Regulatory and Compliance Considerations: Upholding Integrity and Trust
In an increasingly regulated landscape, adherence to data protection policies and industry standards is paramount for organizations embracing WADWARE. Ensuring compliance with regulatory frameworks not only fosters trust among customers and stakeholders but also mitigates legal risks and safeguards reputational integrity.
The Future Landscape of WADWARE: A Glimpse Ahead
Looking ahead stands poised to emerge as a cornerstone of digital transformation, continually evolving to meet the evolving demands of technology. The collaborative efforts of the developer community and industry pioneers will shape the trajectory of influencing its role in the ever-evolving technological ecosystem and cementing its status as a catalyst for innovation and progress.
Embracing the Future with WADWARE
WADWARE represents more than just a technological advancement; it embodies a paradigm shift in how we conceive, develop, and deploy software solutions. While challenges abound on the path to adoption, the promise of unparalleled scalability, reliability, and security positions as a beacon guiding us towards a more efficient, interconnected, and resilient digital future. As organizations navigate this transformative journey, embracing holds the potential to redefine industry standards, drive innovation, and pave the way for a future where possibilities are limitless and boundaries are transcended.
Protecting Your Digital Experience: Shielding Against Wadware
In the realm of software, where innovation intertwines with convenience, there exists a lurking threat wadware. This unwanted software, stealthily bundled with desired applications, compromises user experience, invades privacy, and poses security risks. Understanding the nuances and implementing proactive measures are imperative in safeguarding your digital ecosystem.
Wadware: The Intrusion Within
Wadware, an amalgamation of ‘wad’ (bundle) and ‘software,’ epitomizes the infiltration of unwanted software into our digital landscape. Often bundled surreptitiously during software installations manifests as additional programs or utilities, detracting from the intended user experience and introducing vulnerabilities into systems.
The Bundling Phenomenon
Bundling serves as a covert strategy employed by software developers to expand the reach of their products. Users, unsuspecting during installations, inadvertently opt into the installation through pre-checked boxes or bundled offerings. This insidious practice compromises user autonomy and fosters an environment ripe for exploitation.
Consequences of Wadware Installation
The ramifications of installation reverberate across various facets of the digital realm, from performance degradation to privacy infringements:
System Slowdown and Performance Issues: Wadware clandestinely consumes system resources, leading to noticeable performance degradation and sluggishness.
Privacy Concerns: Many wadware programs engage in data collection, compromising user privacy and potentially facilitating identity theft or unauthorized access to personal information.
Intrusive Advertising and Pop-ups: The proliferation of unwanted advertisements and pop-ups disrupts user experiences, diminishing productivity and inundating users with irrelevant content.
Risk of Malware: In the most severe cases may serve as a vector for malware dissemination, exposing users to security vulnerabilities and compromising system integrity.
Shielding Against Wadware: Proactive Measures for Protection
Armed with knowledge, users can adopt proactive measures to shield against infiltration and safeguard their digital experiences:
Pay Attention During Installation: Exercise caution during software installations, scrutinizing each step and unchecking boxes associated with bundled offerings or additional software.
Download Software from Reputable Sources: Source software from official websites or reputable distribution platforms to mitigate the risk of inadvertently downloading bundled wadware.
Utilize Reliable Security Software: Employ robust antivirus and antimalware solutions to detect and neutralize threats before they infiltrate systems.
Question the ‘Free’ Model: Exercise skepticism towards free software offerings, as they may harbor or engage in data monetization practices detrimental to user privacy and security.
Conclusion
Wadware poses a pervasive threat to the integrity and security of our digital ecosystems necessitating vigilance and proactive measures to mitigate its impact. By understanding the tactics employed by developers and adopting best practices for software acquisition and installation, users can fortify their digital fortresses and navigate the digital landscape with confidence. Together, let us embark on a journey towards a safer, more secure digital future, where remains but a relic of the past, overshadowed by the resilience and ingenuity of vigilant users.
More Stories
Top eSIM Providers for Europe Travel in 2025: Compare Plans & Prices
As global connectivity continues to evolve, eSIM technology has emerged as a game-changer for travelers, offering seamless access to mobile...
Precision Technologies International: Best Innovation Partner
Precision Technologies International (PTI) is the front-end transformer of many industries through innovative solutions. As day and night mark another...
Understanding Cybersecurity Risks: A Comprehensive Guide
In today’s interconnected world, cybersecurity is no longer an optional consideration—it’s a necessity. With businesses, governments, and individuals increasingly relying...
Unlocking Efficiency: How Contract Management Systems Enhance Business Operations
In the ever-evolving business landscape, maximizing efficiency is paramount. With organizations facing mounting complexity and competition, streamlining contracts processes and...
Understanding the CDK Cyber Attack: Implications, Causes, and Future Cybersecurity Threats
In recent years, cybersecurity has become a top priority for businesses and organizations worldwide. The digital landscape is continually evolving,...
Unveiling Crypto-Legacy.App Software: The Future of Cryptocurrency Management
In the rapidly evolving world of cryptocurrency, innovative software solutions are crucial for investors and traders alike. One of the...

